MDR Services Unmasked: Are You Missing Out on Next-Gen Cybersecurity?

 By
Jason Miller
·
9 minute read
By
Jason Miller
·
9 minute read
Did you know that on average there are 130 cybersecurity attacks per organization, per year?
In the world of managed detection and response, the options are vast and varied. Like many businesses, you might find yourself pondering critical questions such as: are MDR services the ideal choice for my organization? Which services are available and best suited to our needs? Who are the top vendors in the industry?
To make an informed decision, it's essential to assess your organization's unique requirements and thoroughly evaluate the available MDR solutions. In this article, we'll guide you through the key considerations and steps to help you choose the right MDR service for your business and stay ahead of ever-evolving threats.
What are MDR Services?
Managed Detection and Response (MDR) services are a type of cybersecurity solution provided by third-party vendors to help organizations proactively detect, analyze, and respond to various cyber threats. MDR services typically combine advanced technologies and human expertise to offer comprehensive protection to an organization's IT infrastructure, including endpoints, networks, and cloud environments.
MDR services detect and respond to known and unknown threats in real time. Moreover, unlike traditional security solutions, which may only address a single type of threat, MDR services are multi-layered.
As a result, they can deliver comprehensive protection against various threats like ransomware and social engineering. One of the key benefits of MDR is its ability to swiftly detect and remediate incidents before they cause damage.
Additionally, MDR services can provide valuable insights into an organization's security posture, helping to identify areas for improvement. As the threat landscape continues evolving, MDR services become crucial to any security strategy.
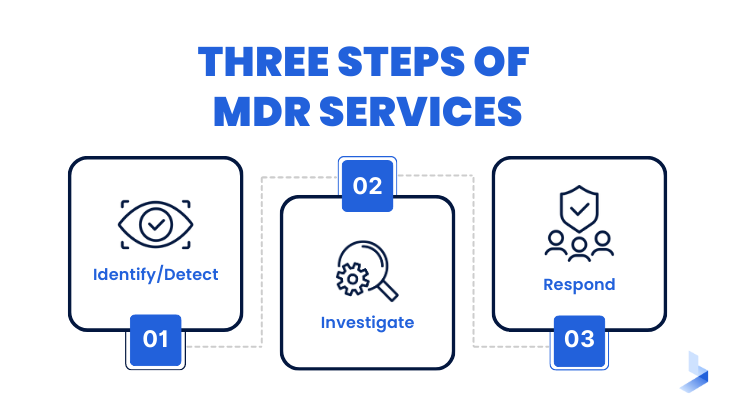
Why the MDR Market Exists
MDR solutions help organizations with potential security incidents by detecting, investigating and responding to threats. Unlike traditional security solutions that focus on preventative measures, MDR takes a more proactive approach by providing visibility into suspicious activity and offering tools for conducting forensic investigations. This solution is becoming increasingly necessary as attackers become more sophisticated and organizations face more pressure to comply with regulations.
As a result, the managed detection and response market is set to grow to $5.6 billion by 2027, according to MarketsandMarkets analysis.
There are several factors driving this growth, including:
- The increasing demand for advanced threat detection and response capabilities
- The need for better visibility into network activity
- The desire to improve incident response times
Furthermore, with the continued rise of cyber-attacks, it's clear that MDR solutions are here to stay.

Technologies Involved with Managed Detection and Response
MDR uses various technologies to detect, respond to, and prevent cyberattacks. By integrating several security tools and processes, MDR provides a more comprehensive view of an organization's security posture. As a result, MDR is often used to supplement traditional security solutions, such as firewalls and intrusion detection systems.
Some common technologies involved in MDR include:
- Data collection and analysis tools
- Threat intelligence platforms
- Incident response automation
Data collection and analysis tools gather data from multiple sources, such as:
- Endpoints
- Networks
- Applications
This data is then analyzed for signs of anomalous activity that may indicate a security incident.
Threat intelligence platforms provide analysts with information about known and emerging cyber threats. This information can be used to improve the organization's detection capabilities.
Finally, incident response automation helps to streamline the process of responding to incidents by automating repetitive tasks, such as malware removal and user notification.
By combining these technologies, organizations can detect and respond to cyberattacks more effectively. Additionally, MDR can help reduce the workload of security analysts by automating many common tasks. As a result, MDR is becoming an increasingly popular choice for organizations looking to improve their cybersecurity posture.
Endpoint Detection and Response (EDR)
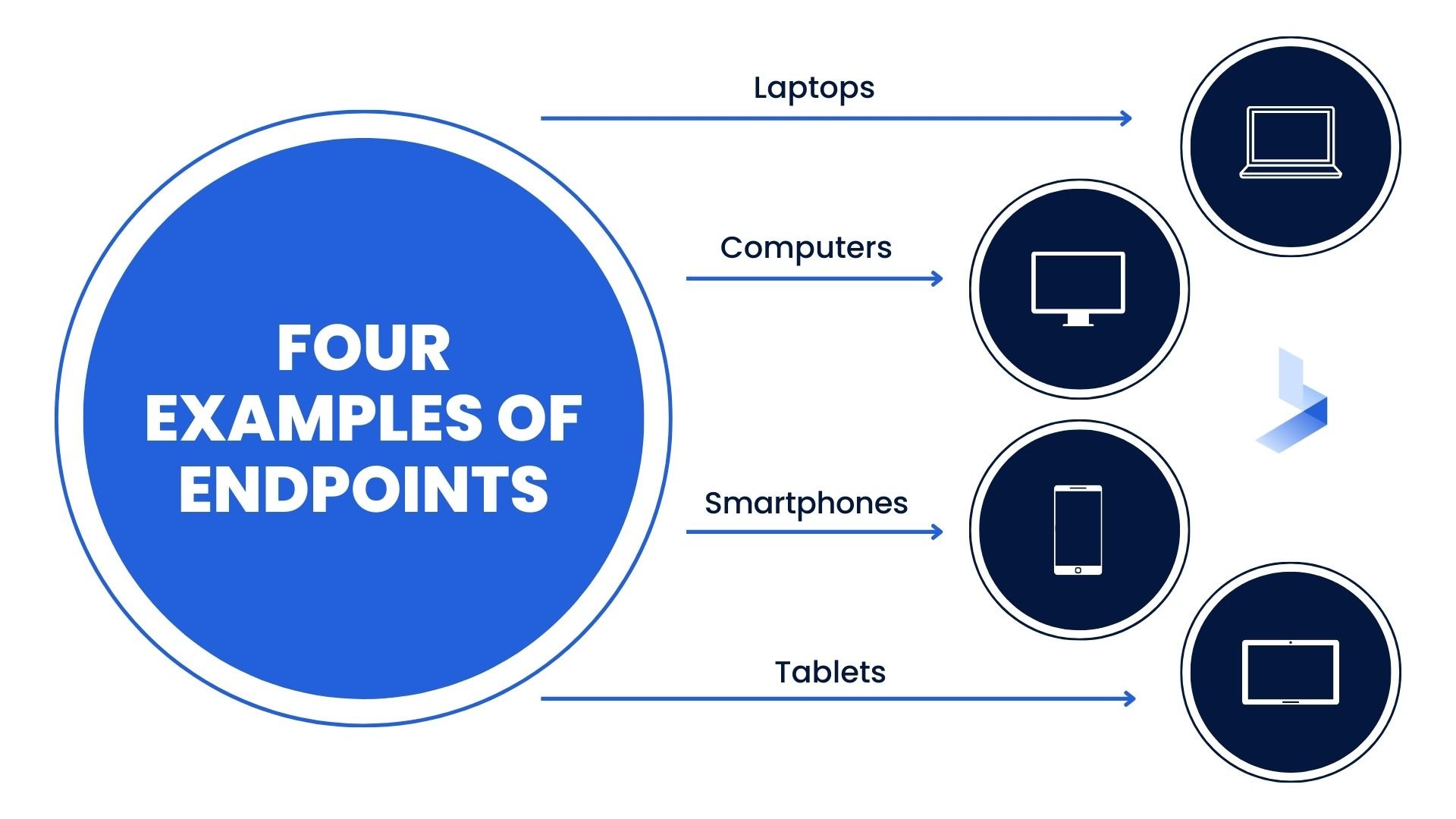
EDR is a technology that helps to detect and respond to endpoint threats. Endpoint threats are a type of cyber attack that targets devices such as:
- Laptops
- Computers
- Smartphones
- Tablets
These devices are often referred to as "endpoints" because they are the end point of a network. Endpoint threats can take many forms, but they all share one common goal: to gain access to the data on the device.
One of the most common endpoint threats is malware. Malware is a type of software designed to damage or disable a computer system. Hackers can install it on a device without the user's knowledge or consent and spread it from one device to another.
Other common endpoint threats include phishing attacks and Denial of Service (DoS) attacks. Phishing attacks attempt to trick users into revealing their personal information, such as passwords or credit card numbers. DoS attacks overload a system with traffic, making it difficult or impossible for legitimate users to access the system.
Endpoint detection and response software are typically used with other security technologies, such as antivirus and firewall protection. EDR uses various methods to detect threats, including:
- Heuristics
- Signatures
- Behavioral analytics
Once EDR detects a threat, it can help to contain and remediate the threat. EDR is an integral part of any security strategy, as it can help to identify and respond to threats quickly.
There are a variety of vendors that offer EDR solutions, and each solution has its strengths and weaknesses. As such, it is important to carefully evaluate each solution to ensure that it meets your organization's needs.
In addition, EDR is a rapidly evolving field, and engineers are constantly developing new solutions. As such, it is important to stay up-to-date on the latest developments in EDR to protect your organization against the latest threats.
Security Information and Event Management (SIEM)
SIEM is a technology that consolidates log data from multiple security products into a central location for review and analysis. This data can include anything from firewall logs to user activity data.
SIEM tools typically offer real-time event monitoring and the ability to run historical reports. To be effective, SIEM solutions must be able to normalize and correlate data from various sources. As such, they often come with built-in or customizable rule sets that help to identify potential security incidents.
While SIEM can be a valuable tool for security teams, it is important to note that it can sometimes generate a high volume of false positives. As a result, it is often used in conjunction with other technologies, such as MDR.
Like SIEM, MDR solutions collect and analyze data from multiple security products. However, they also use machine learning algorithms to help identify anomalies and potential threats.
In addition, MDR platforms typically offer broader coverage than SIEM, including:
- Support for email
- Endpoints
- Networks
By combining the capabilities of SIEM and MDR, organizations can more effectively detect and respond to security incidents.

Threat Intelligence
Early detection and response are essential in protecting your business from cyberattacks. That's why more and more companies are turning to MDR solutions that combine multiple security technologies, including threat intelligence.
Threat intelligence is designed to provide organizations with up-to-date information about emerging threats, vulnerabilities, and attack tactics. This information helps in identifying and prioritizing risks, enabling a more proactive security posture. Key components of threat intelligence include:
- Data collection: Gathering data from various sources, such as open-source feeds, proprietary databases, and industry partnerships.
- Analysis: Analyzing the collected data to identify patterns, trends, and actionable insights.
- Correlation: Connecting the dots between different threat indicators to understand the bigger picture and context.
By integrating threat intelligence into their security strategies, MDR solutions can detect and respond to both known and unknown threats more effectively. This combination of multiple security technologies offers a more comprehensive approach to detecting and responding to cyber threats.
Defining Features of MDR
MDR is a type of threat prevention to identify and block malicious activity that uses a combination of:
- Signature-based detection
- Behavioral analytics
- Machine learning
MDR provides a more comprehensive defense against modern cyber threats. But, first, let's look at a few defining features of MDR services.
Blocks Attacks with Threat Prevention
Traditional security solutions such as firewalls and antivirus software are no longer sufficient to protect against today's sophisticated attackers. Instead, MDR provides a multi-layered defense to detect and block known and unknown threats.
MDR systems continuously monitor network traffic and user activity for suspicious behavior. If an attack is detected, the system will take action to prevent the malware's spread or contain the damage.
MDR can be used to protect against a variety of threats, including:
- Malware
- Phishing attacks
- Data breaches
In addition, using multiple detection methods, MDR systems can provide a more effective defense than any single solution. As a result, MDR is an integral part of any organization's cybersecurity strategy.
Broad Visibility and Contextual Understanding
MDR combines data from multiple security products and provides a more holistic view of an organization's security posture. Unlike traditional security solutions focusing on a single security aspect, MDR provides visibility into all aspects of an organization's security posture. This includes activities from:
- Network
- Endpoint
- User
- Application
By providing this broad visibility, MDR helps organizations to detect and respond to threats more effectively.
In addition, MDR also provides contextual understanding by correlating data from multiple sources. This helps organizations to quickly identify the root cause of incidents and take the appropriate remediation steps.
.png?width=735&height=340&name=MDR%20provides%20visibility%20into%20(735%20%C3%97%20340%20px).png)
Data Retention
MDR solutions typically retain data for a longer period of time than SIEM solutions. This is because MDR systems are designed to provide visibility into past incidents and help with root cause analysis.
This data can be used to improve an organization's security posture by identifying trends and developing new detection rules.
Integrated Threat Intelligence
MDR security systems collect data from multiple sources, including:
- Endpoints
- Networks
- Email systems
This data is then analyzed in real-time to identify potential threats.
As a result, MDR systems are designed to provide a high level of visibility into all aspects of an organization's cybersecurity posture.
In addition, MDR systems typically include features such as:
- Automatic incident response
- Threat intelligence sharing
As organizations increasingly face complex cybersecurity threats, MDR systems are essential to their defense strategy.
Improve the ROI of Current and Future Security Investments
First, it helps to improve the ROI of current security investments. Organizations can save money on licensing and hardware costs by integrating multiple tools into one platform.
Second, MDR helps improve detection and response times by reducing the need for manual data correlation.
Third, MDR provides visibility into the entire attack surface, making it easier to identify and defend against threats.
Simplify Investigation and Response to Known and Unknown Threats
MDR systems are comprehensive, covering everything from known malware to sophisticated zero-day attacks. By collecting data from multiple points in the network, MDR systems can provide a complete picture of what is happening in a system and make it easier to identify and respond to threats.
MDR can also help simplify incident response by automating many of the tasks involved in investigation and containment. As attacks become more sophisticated and challenging to detect, MDR will likely become essential to any organization's security posture.
How MDRs Are Different From Other Security Tools
MDR is designed to provide visibility into all aspects of an organization's IT environment and to detect and respond to threats as quickly as possible. Here's a closer look at how MDRs differ from other security tools.
Most security tools focus on a specific area of an organization's IT infrastructures, such as email or network traffic. MDRs, on the other hand, provides a unified view of all activity across an organization's entire IT environment. This allows MDRs to detect threats that might otherwise go unnoticed by other security tools.
MDRs also can automatically respond to threats in real-time. Integrating MDRs with other security systems, such as firewalls and intrusion detection systems, makes this possible. When a threat is detected, MDRs can take action to contain the threat and prevent it from spreading.
While MDRs offer many advantages over traditional security tools, they are also more complex and expensive. As a result, they are not suitable for every organization. However, MDRs can be a valuable addition to their security arsenal for organizations that are serious about cybersecurity.
Types of MDRs
MDR is a security strategy that aims to give organizations a more comprehensive view of their security posture. MDR systems collect data from multiple sources and use machine learning to detect and respond to threats.
There are three main types of MDR:
- Network-based
- Host-based
- Cloud-based
Network-based MDRs are deployed on an organization's perimeter and collect data from network traffic. Host-based MDRs are installed on individual endpoints and collect data from host activity. Cloud-based MDRs are hosted in the cloud and collect data from cloud-based applications and services.
Each type of MDR has its strengths and weaknesses, so organizations should choose the type that best fits their needs.
Focus On Threat-Centric Use Cases
MDR systems are designed to give organizations a more comprehensive view of their security posture. However, MDRs are not a panacea for all security problems. Instead, they should be used to address specific threat-centric use cases, such as data exfiltration or malware infections.
Organizations can get the most out of their MDR investment by focusing on these types of threats.
Detection
With the rise in sophisticated cyber threats, detection has become more important than ever. However, detection is often difficult, as it requires a deep understanding of the underlying threat landscape.
This is where MDR services can play a vital role. By combining data from multiple sources, MDR systems comprehensively view an organization's security posture. This, in turn, makes it easier to identify and investigate potential threats.
In addition, MDR services can help to speed up incident response times by providing access to real-time data. As a result, they are an essential tool for any organization that wants to stay ahead of the curve regarding cybersecurity.
Alert Triage and Validation
In the world of cybersecurity, MDR systems are the new hotness. These systems provide a comprehensive view of an organization's security posture by integrating data from multiple security solutions. However, MDR systems come with challenges, chief among them being the need to focus on threat-centric use cases.
Alert triage and validation are two key areas where MDR systems can make a real difference. MDR systems can help security analysts quickly identify and prioritize critical incidents by providing a unified view of alerts from multiple sources.
In addition, MDR systems can help to validate alerts by cross-referencing data from different security solutions. As a result, focusing on threat-centric use cases is essential for getting the most out of an MDR system.
Automated Investigations and Response
To effectively investigate and respond to threats, MDR systems must be able to focus on the right use cases. One such use case is the automatic investigation of suspicious activity.
By automating this process, MDR systems can quickly identify the source of a threat and take appropriate action. This not only saves time but also allows security teams to focus their attention on other important tasks.
Another use case essential for MDR systems is the automated response to threats. This includes taking immediate action to contain the threat and taking steps to prevent future attacks. By automating the response process, MDR systems can help organizations reduce their overall risk posture.
Threat Hunting
The collection of data drives effective threat hunting. MDR systems can provide a wealth of data that can be leveraged for this purpose. However, it is important to focus on threat-centric use cases when using MDR data, as this will help to ensure that the most relevant information is being collected and analyzed.
For example, rather than simply looking for signs of malicious activity, a threat hunter may focus on indicators of compromise associated with a specific threat actor.
By doing so, they can more effectively identify active threats and take steps to mitigate them. In short, MDR systems can be a powerful tool for threat hunting, but it is important to use them correctly.
Start Securing Your Organization With MDR Services Today
If you're looking for a comprehensive security solution, MDR is the way to go. With MDR services, you'll have access to all the tools and resources you need to effectively detect and respond to sophisticated threats.
In addition, managed MDR services make use of cutting-edge technologies, such as machine learning and artificial intelligence, to constantly improve the effectiveness of detection and response.
Don't wait until it's too late, start securing your organization with managed MDR today.
Still not sure if managed MDR is right for you? Click here for more information on managed MDR services. Or, contact us today to speak with a managed MDR expert.
