SOAR Cybersecurity Approach for Higher Ed

 By
Jason Miller
·
7 minute read
By
Jason Miller
·
7 minute read
Information security in a college or university presents multiple challenges. There is a large turnover in the user population every year. Students are highly mobile and do a lot of their work without supervision. Many of them love to push the limits of what they can do. For some students, privacy is a critical issue. If IT management in higher education is like herding cats, security management is like protecting the cats from wolves in spite of themselves.
The IT staff that has to deal with the situation is usually pushed to their limit. The staff may not be large enough, and the budget requires making difficult choices. A relatively new but growing approach called Security Orchestration, Automation, and Response (SOAR) offers a better way to use limited resources to maintain acceptable security levels in the context of higher education.
Criminals find it’s worth going after educational institutions, even if attacking enterprises is more lucrative. Schools tend to be vulnerable targets.
IT in higher education
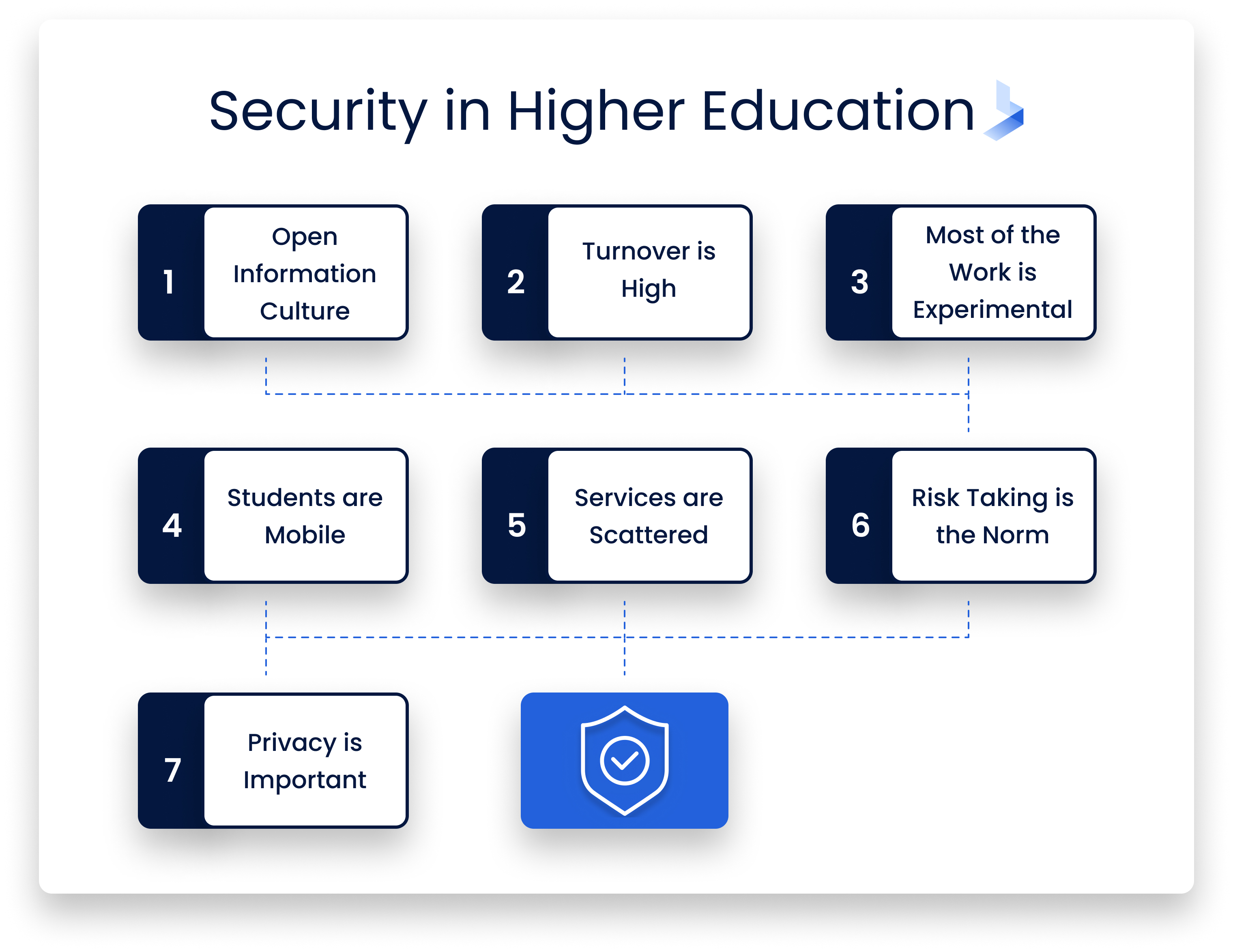
People generally don’t think of educational institutions as having major security issues, but they present a special challenge in many respects.
- The culture is one of open information. Faculty and students expect ease of access, not locked-down systems.
- The turnover is high. Every year a class graduates, a new class comes in, and others transfer in or out. The new students need accounts and passwords. Old accounts need to be closed and their data archived or deleted.
- Much of the work is experimental. Faculty and students create projects, emphasizing quick proofs of concept rather than airtight design. They make their work available quickly without the benefit of QA engineers or beta testers.
- Students are mobile. They may work in classrooms, libraries, and student housing all in the same day. With the pandemic, many students now log in from home. They also make heavy use of wireless connections, both on- and off-campus.
- Services are scattered. Some schools have highly centralized IT services, but others have separate operations in each department and library, or for registration, HR, and student services. Each of these has its own user base and security issues. The central IT department has no control over many of them.
- Risk-taking is the norm. While today’s students enter with years of computer experience, they haven’t necessarily learned caution. Negligence about protecting information is common. They visit questionable sites and use weak passwords. Students can’t be expelled for negligence as lightly as employees can be fired or reassigned.
- Privacy is important. FERPA imposes strict privacy requirements while mandating that students have access to their records. Foreign students may be at risk if their privacy isn’t safeguarded.
The computer systems in a large educational institution aren’t so much a network as a sprawl. It’s a situation that is ripe for accounts to be broken into and security threats jumping from one system to another. Ransomware and other attacks take advantage of the situation and can inflict costly damage. Keeping risks down requires the best technology available.
The problems with conventional approaches
Many small networks rely on nothing more than a firewall and (sometimes) anti-malware software for security. Their operators don’t think of them as targets. Unfortunately, everything is a target. Even if a server contains nothing interesting, it’s a place to put botnet malware and run ransomware. It’s a jumping-off point for attacking other on-campus systems. Anything that runs an HTTP server needs to take security seriously.
Many advanced security tools are available, including monitoring systems, web application firewalls, vulnerability scanners, and CMS plug-ins. They help, but they’re oriented toward a centrally controlled network. Lists of security recommendations often start with “compile an inventory of all systems on the network,” but in an educational institution, that’s usually a hopeless task.
Two difficulties aggravate the situation. One is that threats can move laterally in a loosely managed network. Servers with poor protection are easily penetrated targets, and other servers trust them more than they trust packets from outside. A hastily configured server in the back of an office can expose more valuable servers to risk.
The second problem is that users pose a significant insider risk, more so than in a typical business. Many students are inclined to be hackers in the original sense — people who love playing with systems to see what they can do, probing just for the fun of it. Other motives come into the mix as well: finding the questions on next week’s quiz, tampering with the grading system, and so on. Security systems assume that threats from outside are the big problem, but on campus, disruptions can come from anywhere.
SIEM (security information and event management) systems help to manage security in a complex network. They gather information from many sources and analyze it using a threat intelligence base. Serious problems trigger alerts, and regular reports point out weak points and areas for improvement. SIEM automates threat identification and many incident responses.

However, SIEM by itself is focused more on external threats than on insider actions and human error. It can check and report configuration issues and other weaknesses, but in general, it assumes that the systems being managed are trustworthy until an outside action compromises them.
Other tools cover different aspects of security. Firewalls block malicious IP addresses and close off non-public ports. Spam filters try to keep phishing messages from getting through the school’s email servers. Personal anti-malware software can be made available, but users may or may not put it on their personal machines. The challenge is making everything work together. It’s like a jigsaw puzzle with thousands of pieces.
Orchestrating security with SOAR
The SOAR cybersecurity approach aims at bringing all the pieces together. Again, it stands for Security Orchestration, Automation, and Response. Let’s look at those three aspects.
Orchestration is the big one. SIEM and other tools automate security measures, but cybersecurity orchestration brings independent tools together. In a symphony, the composer may present a theme in the strings, then vary it in the woodwinds and finally give it a triumphant statement in the brass. As the term is used in information technology, it means connecting tools and services so they work together with a minimum of human intervention. The tools may reside on different systems, and they weren’t originally designed with a common purpose. Orchestration creates processes that multiple, independently created services participate in.
Automation of individual tools can work by itself, but SOAR systems make them work under orchestration. Individual services carry out tasks based on a schedule or a triggering condition. An excessive number of login attempts, for instance, could trigger a task that prevents further attempts from the same source.
Incident response is also orchestrated and automated under this approach. Where possible, it handles a security incident automatically, in addition to logging the event or sending an alert. The response could include quarantining the affected system, updating firewall rules, or disabling a compromised account. In many cases, SOAR can determine that an incident is a false positive, requiring no immediate action. It can handle minor incidents without assistance from the security team. Human intervention is still necessary for more important incidents, but even then, automation saves the administrators time and lets them focus on the cause, removal, and remediation.
The goal is to let analysts and administrators work as efficiently as possible with a set of complex, diverse systems. The ideal is a “single pane of glass” — a dashboard that brings together information from all the sources and lets the people in charge review everything at a single glance.
Let’s look more closely at cybersecurity orchestration. Bringing together diverse tools and services reduces the siloing of information. It makes it possible to see not just separate actions but the overall picture. Online threats typically use multiple techniques. They send out phishing emails and probe servers for vulnerabilities. They start by planting a small piece of code that downloads a larger malware program. Hostile code copies itself to other systems and escalates its privileges. The process involves multiple applications and computers.
An anti-malware tool may detect and stop one action, but other parts of the process remain active and find another route. Only a fully orchestrated strategy can catch all the techniques being used and fully eliminate the threat.
SOAR techniques in academia
It may appear at first that SOAR is an expanded version of SIEM. The two technologies borrow from each other, and they may eventually merge. They aren’t the same, though. The emphasis of SIEM is on the collection and coordination of security data from multiple sources to better identify threats. On the other hand, SOAR is aimed at reducing the amount of routine work that administrators and security personnel have to engage in.
One goal of the SOAR cybersecurity approach is to orchestrate frequently used procedures that would otherwise require multiple manually initiated steps. In some systems, this requires skill at Python, Perl, or other scripting languages. The trend today is to support the creation of playbooks, scripting directions created with the aid of a graphic interface. This reduces or eliminates the need for traditional coding. A playbook can be used as a template for multiple tasks, with just minor changes to adapt it to a related situation.
Playbooks can accelerate investigations by orchestrating what would otherwise be a tedious process. A playbook to analyze email for phishing techniques can examine attachments, check headers for suspicious characteristics, and correlate dangerous mail and links with their point of origin. This makes it easier to update spam filters on a regular basis.
Deactivating hundreds or thousands of accounts at the end of the academic year is burdensome, and an incomplete job leaves security holes. Most students will have accumulated multiple accounts and associated files, and it’s necessary to shut down the accounts. Policy dictates whether to delete or archive their files and email. A playbook can reduce all this work to a single process which is less prone to errors.
Case studies
The IT Security Office at Duke University adopted SOAR as a proactive approach to keeping “bad actors” from gaining access. The project is still in its development stages, looking for patterns and trends in logs. The project merged log data with a cache listing bad actors. It was able to identify which systems were being targeted the most. The attackers used multiple methods to penetrate those key systems, while less important targets usually were targeted by just one method.
Some of these systems had as much as 90% of their requests coming from bad actors. The SOAR information let the administrators of those systems add extra measures to keep malicious requests out. As of their latest report, Duke’s Office of Information Technology added two new detection techniques and made a to-do list of signatures for its detection systems.
A 2019 Cyber Intelligence Report from Carnegie Mellon University advises: “When configured appropriately, SOAR technologies can be a force multiplier for organizations with limited staff and time — especially when analysts are drowning in repetitive manual tasks. SOAR technologies automatically connect and coordinate disparate cybersecurity tools, threat intelligence platforms, and other non-security tools and products into a single dashboard. “
Other explorations of the SOAR cybersecurity approach by academic institutions include a session at the University of Arizona 2020 Summit, an online session at Indiana University of Pennsylvania’s CAE Forum, and coverage at the University of Michigan’s Cybersecurity Professional Bootcamp.
How to get started with the SOAR cybersecurity approach
While this approach can save a lot of effort in the long run, adopting and deploying it is undeniably a big task. A SOAR system should work with existing tools rather than requiring a reconfiguration from the ground up. It can start by working with the most critical or work-intensive systems and expand over time to cover more of the school’s IT infrastructure. Doing even that much will free up a great deal of the staff’s time and allow faster resolution of security problems.
BitLyft can help with a free assessment to determine if the SOAR cybersecurity approach is right for your educational institution and how you can deploy it most effectively. A cybersecurity strategy that makes the best use of your resources will decrease employee burnout and reduce disruptions in the educational process.
