CISA Shields Up: How to Respond

 By
Emily Miller
·
13 minute read
By
Emily Miller
·
13 minute read
What would you do if a cyberattack disabled your business? You may think your organization is low-risk for such an attack, but think again.
In response to the growing threat of cyberattacks, the Cybersecurity and Infrastructure Security Agency (CISA) recently launched the Shields Up Initiative, uniting more than 30 countries in a concerted effort to strengthen cybersecurity during this time of unrest.
The White House has issued warnings about potential malicious cyber activity originating from Russia, as the nation may retaliate against the economic sanctions levied due to its military activity. Recent intelligence reveals that Russia could be exploring options for cyber attacks, highlighting the importance of organizations of all sizes taking their cybersecurity systems seriously.
Don't let malware, ransomware, or worse compromise your business; read on to learn how your security team can take necessary measures to combat cybercrime and engage with the CISA Shields Up initiative.
The Launch of Shields Up
Since the inception of the Biden-Harris administration, the government has issued warnings urging organizations to bolster their security measures. In response, the president has issued an executive order aimed at modernizing federal government defenses and enhancing cybersecurity across the board. This has led to the launch of public-private action plans designed to strengthen security in critical sectors such as electricity, water, and pipelines. These plans require agencies to fully utilize their governmental authority to implement new security measures and network defense strategies.
The Shields Up warning is the first of its kind issued by the CISA. It delivers sweeping guidance for people, businesses, and organizations. CISA's Shields Up initiative highlights periods when cyberattacks are more likely to occur and serves as a reminder that we are currently in a time of heightened alert. It is imperative that organizations follow CISA Shields Up guidelines by not only enhancing their cybersecurity but also adhering to IT best practices to ensure robust protection against potential threats.
Why Shields Up?
According to CISA, since Russia invaded Ukraine, there has been an increase in malicious cyber activity worldwide. Since the United States and its allies have imposed economic sanctions to hold Russia accountable for its continued attacks on Ukraine, it is believed that Russia is responding by exploring options for potential cyberattacks.
The invasion of Ukraine started on February 23, 2022. Two days later, the CISA issued a Shields Up warning for US organizations. The rare precaution called for all organizations to prepare for disruptive cyber activity. It applies to all organizations, no matter their size.
This cybersecurity alert was a direct response to increased malicious cyber activity. This activity took place in Ukraine. Some of it included a flurry of DDoS malware attacks.
The CISA believes the United States could become the next target of Russian actors. It also issued a warning about ransomware activity. The activity takes advantage of the current geopolitical disruption.
A Look at the CISA
CISA is the Cybersecurity and Infrastructure Security Agency. Its mission is to understand, manage, and reduce threats to the digital and physical infrastructure of the US.
The agency falls under the umbrella of the Department of Homeland Security. CISA works to connect people and organizations. It provides these individuals with analyses, resources, and tools.
With these resources, organizations can build their own digital communications resilience. They can also improve their physical security. In turn, organizations can maintain a resilient infrastructure for American society.
Which Industries Does Shields Up Affect?
Cyberattacks take advantage of organizations by looking for vulnerabilities within their security infrastructure. The main objective of these cyber intrusions is to find a way into computer systems to destroy or gain control of the systems.
These attacks often block access, steal, or change data. A cyberattack causes a lot of strife among business owners and their IT teams. Yet, you should not feel helpless about a cyber intrusion. CISA Shields Up has been working tirelessly to educate and guide organizations to ensure they do everything they can to prevent cyberattacks.
Schools and Healthcare
Are you a school or a healthcare facility? There is a lot of protected information that needs to remain secure. HIPPA, FERPA, GLBA, and PCI are reasons to take extra measures to keep students and patients safe.
While healthcare facilities are constantly upgrading their security measures, colleges and universities struggle with keeping cybercriminals away. Whether it be a lack of funding for high-end security or the vulnerability students create, higher education institutions are in dire need to up their game.
Manufacturers
Manufacturing companies are often an unthought-of target for cybercrime, but with globalization, they are just as likely to be targeted. In fact, manufacturing companies are considered one of the top targeted sectors for cyberattacks.
Some of the cyberattacks experienced by manufacturing companies include phishing, ransomware, internal attacks, and threats to the supply chain. A lot of these attacks are financially motivated, and they play havoc on company infrastructure.
Energy and Public Utility Companies
What happens when all the lights go out? If a cyberattack was to shut down the electrical grid, people could start to panic. Thankfully, energy and utility companies take a lot of security measures to keep the grid up and running.
Energy and utility companies have some strict regulations to meet. Yet, they still succumb to ransomware attacks, particularly public utilities. With tight budgets and minimal security measures in place, municipal utility companies have become an easy target for cybercriminals.
No Organization is Exempt
CISA recommends that all organizations take quick action to protect their assets. Any business, big or small, can be affected. The key to handling cyberattacks is to have a response plan in place.
CISA has been working hard to bring awareness to large and small businesses about the threats of cyberattacks. No longer do organizations need to apply a wait-and-see approach to cyber security. Instead, they can be part of the solution.
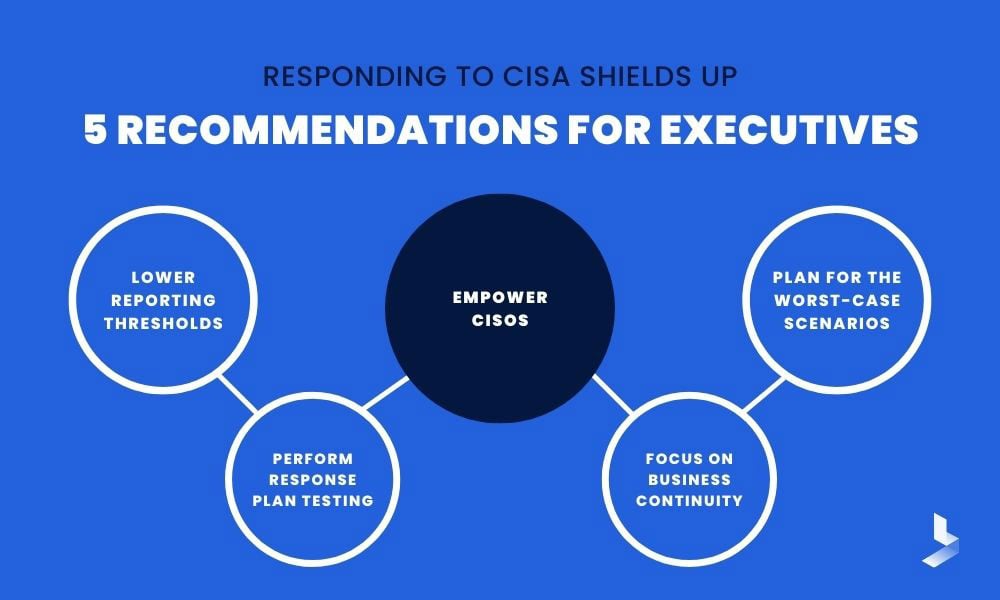
Responding to CISA Shields Up: Key Recommendations
The Shields Up warning covers five key recommendations for leaders. These recommendations include:
- Empower CISOs (Chief Information Security Officers)
- Lower reporting thresholds
- Perform response plan testing
- Focus on business continuity
- Plan for the worst-case scenarios
It’s critical to understand each element of these recommendations. Let’s have a closer look at them.
1) Empower CISOs
Most organizations weigh security improvements against cost and operational risks. Leaders should empower CISOs in this heightened security environment. They must include them in the risk decision-making process.
It’s also vital your entire organization understands security investments are now a top priority.
Historically, security tools and processes have created friction in organizations. As a result, there’s been a widespread barrier to adoption.
Now, however, it’s vital to reassess risks and security posture. Organizations must rethink their trade-offs between security and operations.
More CISO-Related Concerns
In light of the Shields Up warning, CISOs must conduct a full risk assessment of all IT and physical and virtual devices. CISOs must understand the level of risks they’re accountable for. These include risks of data loss and non-compliance.
CISOs must document and identify all threats. These threats could include:
- Ideologies
- Malicious actors
- Nation states
The CISO must figure out how these threats can affect their organization. They must also figure out the right security and compliance frameworks for which they’re accountable.
As a result, organizations must ensure that CISOs have sufficient resources. These resources must suffice to address the risks facing your organization.
Fortunately, vendors have reduced points of friction greatly. Security has become more sophisticated. It’s become easier to deploy security tools.
Firms now deal less with device-level instrumentation and awkward user authentication. Furthermore, companies are better equipped to monitor and pinpoint malicious activity across networks. Whether on-premises or in the cloud, nimbler security tools have helped ease the friction involved with security tools.
2) Lower Reporting Thresholds
The CISA suggests every organization should have documented thresholds. They should use them for reporting cyber incidents to management and the government. However, the threshold is lower in this heightened threat environment.
Leaders must establish an expectation for their personnel to report any indications of malicious activity to the CISA or FBI. By lowering reporting thresholds, companies can ensure the immediate identification of issues. They can also protect against further attacks and victims.
Today, organizations face several reporting requirements. These requirements include frameworks from the:
Now is a time of heightened threat activity. Organizations must report events to the proper government agencies. The reports can give guidance to other organizations, protect consumers, and stop future attacks.
Shields Up Documentation
Companies must document internal and external reporting thresholds based on several criteria. These criteria include:
- Threat levels
- Threat actors
- Compliance requirements
- Enterprise risks
Furthermore, organizations must translate the thresholds into graduated reporting groups. You can base the thresholds on the total risk level.
Also, leaders should work with local federal law enforcement cyber agencies. Ideally, they should work with the local FBI InfraGuard coordinator. Leaders should also join threat forms, such as the ISAC, FBI InfraGuard, and SANS.
When it comes to reporting to federal law enforcement, it’s better to risk overreporting than to underreport.
Companies should use multiple data sources as part of a comprehensive incident response strategy. These sources can help accelerate the identification of compromised systems. Network intelligence such as our XDR with BitLyft AIR platform can support this process.

3) Perform Response Plan Testing
According to the CISA, your response plan should include your security and IT teams. However, it should also include your leaders and board members.
Your senior leadership should participate in a tabletop exercise. The exercise will make sure they’re familiar with how your organization manages major cyber incidents.
The exercise should include a response plan for your company. It should also include a response plan for cyber breaches that might occur in your supply chain.
Tabletop exercises are a vital mechanism. They ensure readiness for cyber incident responses.
Your organization should designate a crisis response team. The team will serve as a frontline for coordinating your response strategy.
Your team should include front-line security responders. It should also include IT operations and DevOps. Furthermore, you should include your communications and legal team.
You must figure out who’s responsible for communicating with your key constituents. These constituents include customers, shareholders, and even your staff.
Planning for Security
The CISA recommends organizations develop several plans. For instance, you should develop an organizational Continuity of Business Operations Plan.
You should also develop a Crisis Management and Communications Plan. Furthermore, organizations should develop a Disaster Recovery Plan. The plans should cover mission-critical technologies and production capabilities.
Organizations should also develop an Incident Response Plan for security incidents. You can use the NIST’s Computer Security Incident Handling Guide for this plan.
Make sure you record what you’ve learned from your tabletop exercises. You can use this information to inform and improve your contingency plans.
You can also use this information to incorporate internal and external stakeholders into your crisis plans. Internal stakeholders might include your incident response team. Meanwhile, external stakeholders might include your company’s attorneys.
4) Focus on Business Continuity
Firms have finite resources. You must focus those resources on your security and resilience systems that support your critical business functions.
Leaders must make sure to identify these systems. They must also ensure staff conducts continuity testing.
Furthermore, it’s essential to ensure critical business functions remain available. You must ensure your network functions after a cyber attack.
You should conduct a Business Impact Analysis before beginning any of your planning. This analysis will help you pinpoint your most critical business and operations systems.
Continuity Considerations
You must use your Business Impact Analysis to ensure you have sufficient processes. These processes include:
- Protective resources
- Compensating controls
- Redundant systems
- Backup recovery controls
You must implement these processes to ensure the resilience of your organization’s critical systems. Here again, you can refer to the NIST’s Computer Security Incident Handling Guide.
With these points in mind, identify the leadership responsible for your critical business systems. You must hold them accountable for the resilience controls of these systems.
5) Plan for the Worst Case Scenarios
The CISA recommends organizations prepare for a worst-case scenario. Leadership should make sure they can take urgent measures.
These measures must protect your organization from losses during an intrusion. They could include disconnecting the high-impact parts of your network.
Until recently, most advanced attacks included software supply chain compromises. Alternatively, they may have included the use of zero-day exploits.
Most often, nation-state actors committed these acts in either case. Now, organizations must harden their systems against cross-border threats.
With these highly sophisticated and damaging attacks, Russia has been a major player in the cyber landscape for some time. So far, US intelligence has not warned of an imminent attack. However, Russia’s history is a strong indicator of what could come.
Consider Organizational Impact
In this heightened threat environment, there are a few things you should consider. For instance, you must communicate your continuity plans to your entire staff.
You should also know most cyber breach intrusion insurance policies don’t cover acts of war. You can’t transfer this risk with security insurance. You can only remove the risk or manage it.
It helps to segment your network. You should also restrict access to and from the internet and company mobile devices. These are ways to control against possible cyberattacks.
Furthermore, you should monitor your network continually. You can do just that with our extended detection and response software. It can help you monitor your network for behavioral anomalies.
Assessing the Current Environment
It’s essential to figure out your risk management strategy. You must identify and understand your risks. You must also think about how much those risks can cost your organization.
Furthermore, you must determine the right security framework for your needs. There are several robust frameworks available, including:
- Center for Internet Security (CIS)
- ISO 27001/2
- NIST SP 800 53R5
- The NIST Security Framework (CSF)
- Top 18 Critical Security Controls
Regulatory compliance does not equal effective security. You must implement these measures along with any frameworks needed for regulatory compliance.
Managing Your Assets
You’ll need operational and technical resources to minimize risks to your security framework. As a result, you’ll need buy-in from executive leadership.
Your security leaders can use the CISA’s Shields Up recommendations and other guidance. This information will help communicate risks and priorities.
You should also keep an ongoing inventory of your assets. This is the process of finding, documenting, and keeping an accurate inventory. Your inventory might include:
- Applications
- Cloud assets
- Devices
- User accounts
- Vendors
The inventory process is critical for knowing what’s connected to your environment and who has access to it.
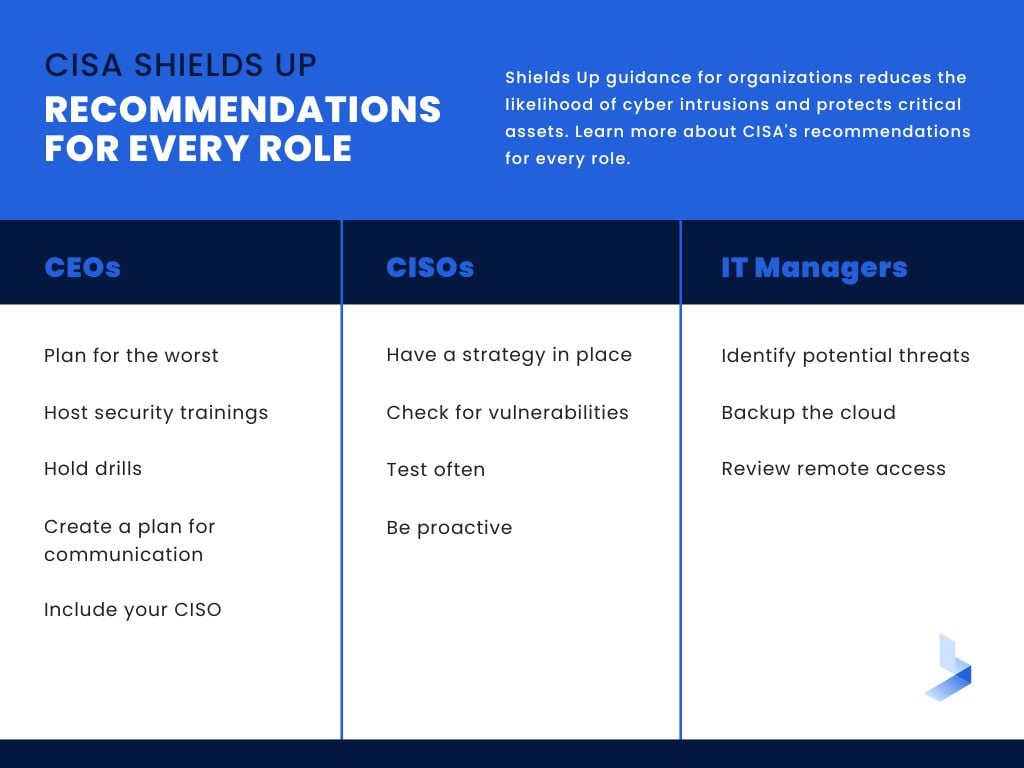
Recommendations for CEOs, CISOs and IT Managers
In light of the CISA Shields Up initiative, it is crucial for organizations to recognize the pivotal roles that CEOs, CISOs, and IT directors play in fortifying cybersecurity measures. This section delves into the responsibilities and actions these key leaders should undertake to ensure a proactive and coordinated response to potential cyber threats, safeguarding their organization's digital assets and infrastructure.
How CEOs Should Respond
As the head of your company, you have worked hard to build what you have. Taking care that your assets are protected is extremely important to you. Do not let a cyber attack ruin your business.
Plan for the Worst
Think about what your worst-case scenario would be. Who or what would be affected? Chances are, it is not just your business accounts that would be at risk. You must think about all the information you have stored about your clients, financials, employees, and the rest of your business.
Will a cyber attack crush your organization? Not if you have a plan. CISA Shields Up informs us that being proactive can help you and your team navigate all the troubles that occur during a cyberattack.
Security Trainings
Implement regular security trainings with your Chief Information Security Officer (CISO) and IT team. During these trainings, discuss email security and phishing, physical access to computers and devices, malware and ransomware, social media, and mobile security. Ensure your team uses multi-factor authentication, and IT keeps up with logs and analytics.
Hold Drills
During an emergency, you need to know what to do. This goes for anything from a simple water leak to the complete disabling of your business. So, how do you ensure that everybody knows what to do during a cyber attack?
First, make sure you have a crisis-response plan and a dedicated response team. Ensure that not only IT is involved, but your senior leadership staff is also. Also, host some tabletop exercises to ensure everybody knows what to do.
Communication
As the CEO, you need to consider how you will respond to the media in the event of a cyber attack. Chances are, there will be confidential information that will be compromised as a result. Be truthful and forthcoming about what happened.
Your team needs to be up to speed on what is happening in the event of a cyberattack. To make this happen, you must have a communication plan in place to broadcast a cybersecurity alert to your team.
At the worst, a cyberattack will disable your entire network. Your organization may temporarily be without email, phone, or Internet. Your leadership and IT team should keep each other's contact numbers and emails on their cell phones if they need to contact somebody during an emergency.
Include Your CISO
Whatever you do, do not leave your CISO out of the loop. Make sure that you include them at leadership meetings and allow them to have a say in the decisions regarding IT and security. Ensure your CISO and IT team are working closely to avoid communication gaps.
Hold regular meetings with your CISO. Ask them the hard questions. How long will it take to get back up and running in the event of a cyber intrusion?
How will you restore the system? Will long will it take, days or hours? Are there ways to backup the system to get back on track quicker? Knowing how a cyberattack will be resolved creates peace of mind.
How CISOs Should Respond
The CISO is responsible for ensuring that there is a security strategy in place and data assets are protected. In case of a cyber attack, the CISO is the one who best understands cybersecurity. So, how should the CISO respond?
Have a Strategy In Place
The CISO needs to create a strategy, policies, and systems to ensure a cyber attack does not happen. However, if an attack does happen, you need to know how to deal with it. Communication is key.
Work with the CEO to create a solid cybersecurity strategy. Create logs and documentation. Present plans and ideas to strengthen your security team and systems.
Staying up-to-date on security trends is one of the most essential things a CISO can do for an organization. Failing to do so opens organizations up for cybercrime. Ensure your IT team is up-to-date on their security and regulatory requirements.
Check for Vulnerabilities
The CISO also needs to check for vulnerabilities and have a program in place to implement security patches. Security patches should be the number one priority for your IT security team. They should be applied as soon as possible.
You should also use your budget wisely. Creating a rock-solid cybersecurity program for your organization will mitigate many risks.
Test Often
Decide on how often to test your emergency response system. The senior leadership team, CISO, and the IT team need to work closely together on this. You will need to test your workflows and backup procedures.
Be Proactive
Most importantly, be proactive and create adequate documentation focusing on your business's critical infrastructure. What data is the most important for your organization to get back online first?
Also, what do already have that can help prevent a complete organizational shut-down? Are there manual controls in place to ensure critical operations continue to run? You should have systems in place to allow for the organization to stay up and running while the IT team is solving the security threat.
How IT Managers Should Respond
The IT team is the first line of defense for keeping your business safe from a cyber attack. They are the ones that keep your software up-to-date, prioritize your updates, and address any vulnerabilities in the system.
Identify Potential Threats
With that said, it is the responsibility of the IT manager to notify the upline of any potential problems or threats to security. As an IT manager, you need to ensure that your team reports any unusual or unexpected activities, even if they were blocked.
One of the biggest downfalls of a cybersecurity team is becoming complacent. Keeping your IT team motivated can keep them from letting down their guard. Overlooking a problem that seemed minor at the time can cause trouble for your organization.
Backup the Cloud
Many organizations store their data on cloud storage services. It is the age we live in. Though the data is encrypted, regularly backing up your data to a physical hard drive will ensure the organization's data is safe.
Review Remote Access
Are there employees who work from home? Your team should review remote access points and install antivirus and anti-malware software on your systems. It is best if employees use company-owned devices at home, but if not, a secure VPN or direct application access are good options.
If working with third-party vendors or other countries, the IT team needs to ensure that remote access points are secure and keep a close eye out for suspicious activity. Enabling your team to keep logs will go a long way.
Your Partner in Cyber Threat Mitigation
How BitLyft Can Help Prevent Cyber Attacks
Detection and response are key before a cyber attack even happens. Fortunately, your organization does not need to carry all the burden on its shoulders. BitLyft's managed detection and response (MDR) solution is designed to keep your organization protected.
However, we take extended detection and response services to a different level. Our team is experts in the cybersecurity realm. We want to ensure all businesses–big or small–have access to the best cybersecurity out there.
Greater Visibility
BitLyft utilizes SIEM technology to ensure your organization has real-time access to what is going on in your network. We provide you with a dashboard including real-time reports and threat alerts.
Quick Response
BitLyft uses security automation to combine multiple tasks and processes into a single event. The software is faster at stopping threats in their tracks. Handling these tasks via automated software accomplishes remediation faster than it would take humans to perform.
Access to the Experts
BitLyft's security operations center team is highly knowledgeable in SIEM, threat hunting, alarm investigation, and remediation. A dedicated cybersecurity team provides protection, detection, knowledgeable guidance, feedback, and direction. Your company will be in the best position to fight against cybercrime.
Accessibility
BitLyft grows with your organization–large or small. We ensure that every organization has access to expert cybersecurity, no matter the time of day.
Please think of us as an extension of your team. We offer team calls, reporting, and check-ins. And if you ever need us, we are just a phone call away.
If you need assistance in navigating the implications of CISA Shields Up, our team of cybersecurity experts is here to support you. Reach out to us today, and we'll help you implement a robust managed detection and response strategy, ensuring your organization's security remains uncompromised.
