Top 7 Cyber Attacks Threatening Manufacturing Companies

 By
Jason Miller
·
10 minute read
By
Jason Miller
·
10 minute read
While financial institutions, medical facilities, and even retail chains have been forced to face the dangers of cyber attacks, manufacturing companies spent most of the last decade blissfully unaware of the likelihood of attack. The reasons for this were mostly two-fold. First, the very real lack of connection between manufacturing companies and the outside world created a comfortable barrier between cyberattacks and manufacturing companies. Second, manufacturing companies mistakenly believed they didn't have much to offer cyber attackers.
In the past, manufacturing companies were connected within the network of a single organization, but a connection with the outside world through the internet was limited. Customer-facing businesses like those in the financial and medical industry didn't have this barrier, making them an ideal target for hackers. However, as technology evolved, and Industry 4.0 seeps into every corner of the manufacturing industry, this old way of communicating is obsolete. In today's connected world, manufacturers are forced to utilize connectivity in a broad variety of ways. The combination of the industry's lack of preparation and vast array of potential vulnerabilities through various endpoints makes manufacturing companies ideal targets for hackers.
The mistaken idea that manufacturing companies had little to offer was mostly baseless. While manufacturing companies aren't in charge of large amounts of money or potentially risky financial transactions, they harbor a wealth of information that hackers can use to extort millions. For many manufacturing companies, learning their potential value has been an expensive lesson. As cybercrime against the manufacturing industry reaches maximum levels with no signs of slowing, these companies are forced to face the facts. Cybersecurity in the manufacturing industry is essential, and it should be utilized sooner rather than later.
Cybersecurity for Manufacturing
If manufacturing companies were comfortable with the idea that they were safe from cyberattacks, this notion is quickly being erased. Awareness of the effects of Industry 4.0 and the increase of cybercrime slowly came to light in 2017 and 2018. However, many companies in the industry remained unaware of the risks.
By 2019, the manufacturing sector reached the top 10 status as the 8th most targeted industry by cyber attackers. The problem exploded in 2020 when many companies were forced to depend almost entirely on remote workers due to pandemic restrictions. While most of the world was largely unprepared for the effects of COVID-19, cyber attackers were ready. The manufacturing industry moved from the 8th most targeted industry by cyber attackers to number 2, falling behind only finance and insurance. According to the 2021 Global Threat Intelligence Report (GTIR), this represents a 300% increase in a single year.
.jpg?width=1080&height=500&name=Untitled%20design%20(4).jpg) The potential impact of these threats on the nation's critical infrastructure and government agencies hasn't gone unnoticed. Although slow to respond to cyber threats in the past, government agencies are beginning to impose stricter regulations for companies that protect sensitive data. The Cybersecurity Maturity Model Certification and the IoT Cybersecurity Act were both introduced during 2020 as a way to introduce minimum cybersecurity regulations for companies that work with government agencies. Still, the full volume of these regulations won't be realized until 2022 and 2026. In the meantime, threat actors will continue to target companies that have failed to heed the warnings and put cybersecurity systems in place. For manufacturing companies aiming to eliminate the risks, there is only one solution. Learn the potential cybersecurity risks for manufacturing companies and build a complete cybersecurity solution to identify and halt threat actors before your network is infiltrated.
The potential impact of these threats on the nation's critical infrastructure and government agencies hasn't gone unnoticed. Although slow to respond to cyber threats in the past, government agencies are beginning to impose stricter regulations for companies that protect sensitive data. The Cybersecurity Maturity Model Certification and the IoT Cybersecurity Act were both introduced during 2020 as a way to introduce minimum cybersecurity regulations for companies that work with government agencies. Still, the full volume of these regulations won't be realized until 2022 and 2026. In the meantime, threat actors will continue to target companies that have failed to heed the warnings and put cybersecurity systems in place. For manufacturing companies aiming to eliminate the risks, there is only one solution. Learn the potential cybersecurity risks for manufacturing companies and build a complete cybersecurity solution to identify and halt threat actors before your network is infiltrated.
The Top 7 Cyber Attacks for Manufacturing Companies
For many manufacturing companies, the biggest cyber threat is a lack of knowledge and training. All too often, management isn't even fully aware of the risks, and most employees have little to no training regarding how to identify and avoid potential threats. Learning the top cyber attacks for manufacturing companies is the first step toward building a cybersecurity solution to protect your business.
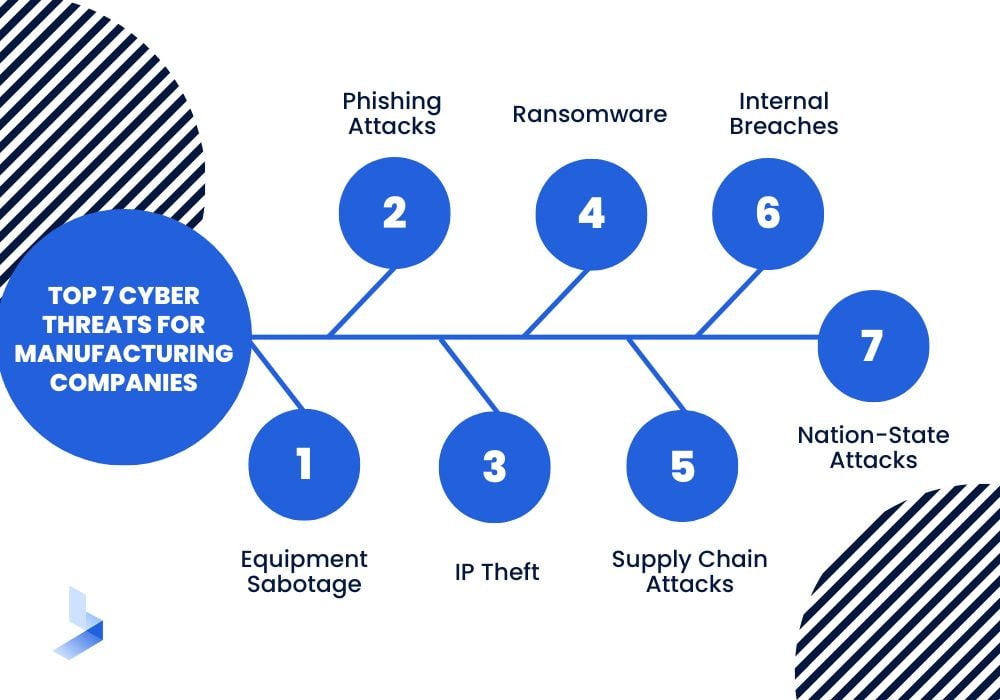
Phishing Attacks
Phishing is one of the oldest and most widely used tactics among cybercriminals. While most people are aware of the way phishing works, many don't realize how advanced the methods have become. Within commercial enterprises, phishing emails most often appear to come from within the company or from an organization likely to do business with the company. These emails look official, have all the right logos, and with a simple click, can prompt employees to provide hackers with a discreet entry point into the network. Unfortunately, this is only where the danger begins. Once threat actors have access to the network of an organization, they can often move invisibly through the network until they gain access to information that will allow them to complete an attack.
As if the nature of these attacks wasn't a big enough threat, there are also a variety of reasons that manufacturing companies are uniquely vulnerable to phishing attacks. Consider these ways manufacturing companies are more vulnerable to phishing attacks than other industries.
- Lack of preparation throughout the industry
- The use of systems never intended to be connected with the outside world
- A long supply chain with many interconnected companies
- Hackers can often access the names of management employees to impersonate
- Fragmented systems across different departments make it difficult to apply a single security framework
Ransomware
As threat actors moved away from the sale of sensitive and financial information as a primary reason for cybercrime, the value of ransomware became evident. Unfortunately, manufacturing companies have much to lose from such an attack. Ransomware is a type of malware that encrypts files on a network and makes them unusable until the demands of hackers are met. These threat actors may threaten to sell or leak sensitive data if a ransom (often millions) is not paid. Another way ransomware users attack manufacturing companies is they make the network unusable to the company until the ransom is paid. This tactic is very effective within the manufacturing sector because downtime puts such a strain on manufacturing companies.
Ransomware attacks often occur on weekends or holidays to allow threat actors to complete as much damage as possible before the attack is realized. This allows hackers to be waiting comfortably when the attack is realized during a busy time for manufacturing organizations. The reasons that manufacturing companies are such an attractive target are many. A vast network of OT devices throughout a long supply chain provides multiple endpoint vulnerabilities, and fragmented systems leave gaps in security.
However, even beyond the potential vulnerabilities, manufacturing companies provide hackers with optimal reasons to target them for a hefty ransom. For manufacturing companies, time is money. To that end, downtime is particularly expensive. Even when ransomware actors demand exorbitant amounts of money, it's often more cost-effective for manufacturing companies to pay up. Unfortunately, downtime may not be the biggest worry for the manufacturing sector. With long supply chains depending on parts or products, other companies and industries can become affected by the disruption within days. This impact can be devastating to the original victim company as business relationships are lost and customers learn of the breach. All too often, manufacturing companies reveal little or no information about ransomware attacks in hopes to salvage their professional reputation.
Internal Breaches
While the majority of cyberattacks are the work of external actors, nearly 30% of attacks come from employees or other personnel with access to the company. As with external hackers, the reasons for these attacks are often financially motivated. However, some employees or former employees launch attacks against a company out of anger or dissatisfaction.

Internal threat actors don't need to gain access to a network. Instead, they can use their existing knowledge or credentials to reach sensitive data. With existing credentials, a threat actor is more likely to invisibly carry out a threat without detection. Unfortunately, even former employees can typically gain this access if passwords or entry methods aren't changed to avoid the potential of such attacks.
The use of personal devices and the increase of remote work has also introduced more ways that employees can unintentionally become the vessel for an internal breach. Most companies were completely unprepared for the regulations that came along with a global pandemic. As manufacturing companies sought ways to stay afloat by maintaining employees remotely, few had the technological equipment to set every worker up with the same security that exists within the company. Many home-based employees found working from home no easy task as lines between personal and work time blurred and became non-existent. For hackers, these home networks and the use of personal devices with limited security provided a new way to access sensitive data from companies large and small.
Equipment Sabotage
Operational technology (OT) provides a wealth of benefits for manufacturing companies. Unfortunately, it can also provide new vulnerabilities for hackers to exploit. OT devices aren't new. However, they are new to the external linking technology of modern communication systems. In the past, these devices didn't require security measures designed to protect them from outside threats. Unfortunately, this means that manufacturing companies often still use them with the same lack of security practices. While there are some concerns surrounding attacks that utilize OT devices as a way to gain access to a network, the implications of danger due to equipment sabotage are far more sinister. When devices are managed and controlled with the use of connected devices, there is potential for damage from malicious attackers with an intent to make devices behave harmfully.
The most well-known examples of this type of malware include Stuxnet and Triton. Stuxnet was the first known use of software designed to interrupt operational technology and was launched against an Iranian nuclear plant in 2010, causing hundreds of centrifuges to spin out of control and self-destruct. Triton was first identified in a petrochemical plant in 2017 when it was used to override essential safety shut-down equipment. The implications of the use of this type of malware in the hands of malicious actors are chilling. The ability to attack safety systems remotely could potentially lead to catastrophic industrial failures with mass casualties.
Unfortunately for those in the manufacturing industry, this makes a potentially dangerous job vastly more threatening. As threat actors continue to develop ways to discreetly access networks, a variety of manufacturing companies could be at risk simply because of the products they produce or equipment used for production. Even worse, equipment sabotage with the intent to cause harm is limited to the manufacturing sector and possibly utilities. This means the security for these attacks is underdeveloped in comparison to attacks that have been targeting financial and retail companies for decades. The only real protection against such attacks is the ability to recognize the threat and eliminate potential vulnerabilities in the system.
IP Theft
The theft of intellectual property (IP) is a type of information theft more likely to go overlooked than the theft of customer data. Yet, it's a serious crime that can damage a company significantly. Your company owns the intellectual property that makes your products or services innovative. That information can be valuable in a variety of ways. As cyberattackers learn new ways to enter a network without detection and discreetly move laterally throughout the system, the dangers of potential IP theft grow. Hackers can quietly mine the information they need over time and even exit the system without detection. This can lead to data that is stolen or altered without detection until your company's trade secrets are used elsewhere.
IP theft is especially important in the manufacturing sector because your company's intellectual property is what differentiates you from the competition. Still, information used to run your company or create your products can be difficult to protect. After all, employees must have access to vital information to complete daily tasks. For manufacturing companies, IP theft can be one of the most damaging types of cyberattacks. Today's technology allows attackers to strike quickly, reproduce or transfer information in seconds, and can be difficult to prove.
The reasons attackers target certain manufacturing companies vary. For instance, a competing company can use your information to reproduce a similar product or create your product more rapidly. When theft includes trade secrets instead of copyrighted information, the crime can be difficult to prove. Manufacturing companies that complete contracts for the DoD or other government agencies are at risk of attacks from nation-state actors. These attacks can be motivated by a desire to gain military secrets or by friendly nations seeking an economic advantage.
Supply Chain Attacks
Cyber threats for manufacturing companies that target multiple groups at once are some of the most widespread and effective attacks that exist today. Supply chain attacks interrupt one link within an organization's supply process to cause a massive disruption that can affect thousands of people. Manufacturing companies are particularly vulnerable to supply chain attacks due to long supply lines and fragmented security systems. With a variety of vulnerable endpoints, hackers can gain access to major companies through partners and suppliers. Supply chain attacks are a double-edged sword since once the main company is forced to shut down operations, each company they supply is similarly affected within days of the initial attack.

Some of the most high-profile attacks in recent months have been supply chain attacks that affect multi-million dollar corporations, critical infrastructure, and even global food production. For many, the Solar Winds attack that infected a trusted software update used by many well-known companies was a much-needed glimpse into the potential dangers of a supply chain attack. In May 2021, a supply chain attack on Colonial Pipeline shut down 45% of the fuel supply in the Eastern U.S., clearly echoing fears of the potential damage of a supply chain attack that affects the nation's critical infrastructure. The gas line attack was followed almost immediately by a cyberattack on JBS Foods, one of the world's biggest suppliers of meat. Both of these attacks were resolved quickly with the payment of millions to hackers. However, the potential dangers of more severe attacks are clear. Successful attacks with malicious intent beyond extortion could cause long-term shutdowns to critical systems and food chains to multiple nations.
Nation-State Attacks
Perhaps some of the most dreaded cyberattacks that exist today, nation-state attacks are cyberattacks carried out by the government or threat actors employed by the government of another country. The motivation for these attacks varies widely and can range from monetary value to intellectual property theft of defense weapons, or even a grudge. Hackers look for any data that will benefit their country's economy and strengthen both key business and military strategies. Nation-state hackers have been known to attack government agencies, critical infrastructure, and virtually any industry known to hold sensitive information.
Nation-state attacks are particularly dangerous for several reasons. The implications of potential dangers associated with the attacks are obvious. Yet, other factors of these well-organized groups are often overlooked. Nation-state threat actors are well-funded, highly trained, and have access to high-tech tools that could make them more difficult to detect. International trade tensions and increased competition for essential goods fuels the interest in these attacks in many manufacturing organizations. However, the threat of nation-state cyber warfare attacks has the potential to do the most damage. These attacks can shut down critical national infrastructures like energy, transportation, military contractors, and government operations.
Protecting Your Manufacturing Company Against Cyber Threats
The dangers of cyberattacks for manufacturing companies are clear. Unfortunately, protecting organizations against such threats isn't quite as transparent. Certain companies are subject to CMMC guidelines and the regulations imposed by IoT Cybersecurity while others are not. Yet, all manufacturing companies need high levels of cybersecurity to protect against the same threats. Luckily, there are things you can do to guard your company against increased threats.
Steps to Improve Cybersecurity Awareness within Manufacturing Companies
While you may not have a comprehensive security plan in place or an in-house cybersecurity plan, there are ways you can protect against cyber threats for manufacturing companies. These steps can help you build awareness of potential threats and recognize any potentially dangerous activity.
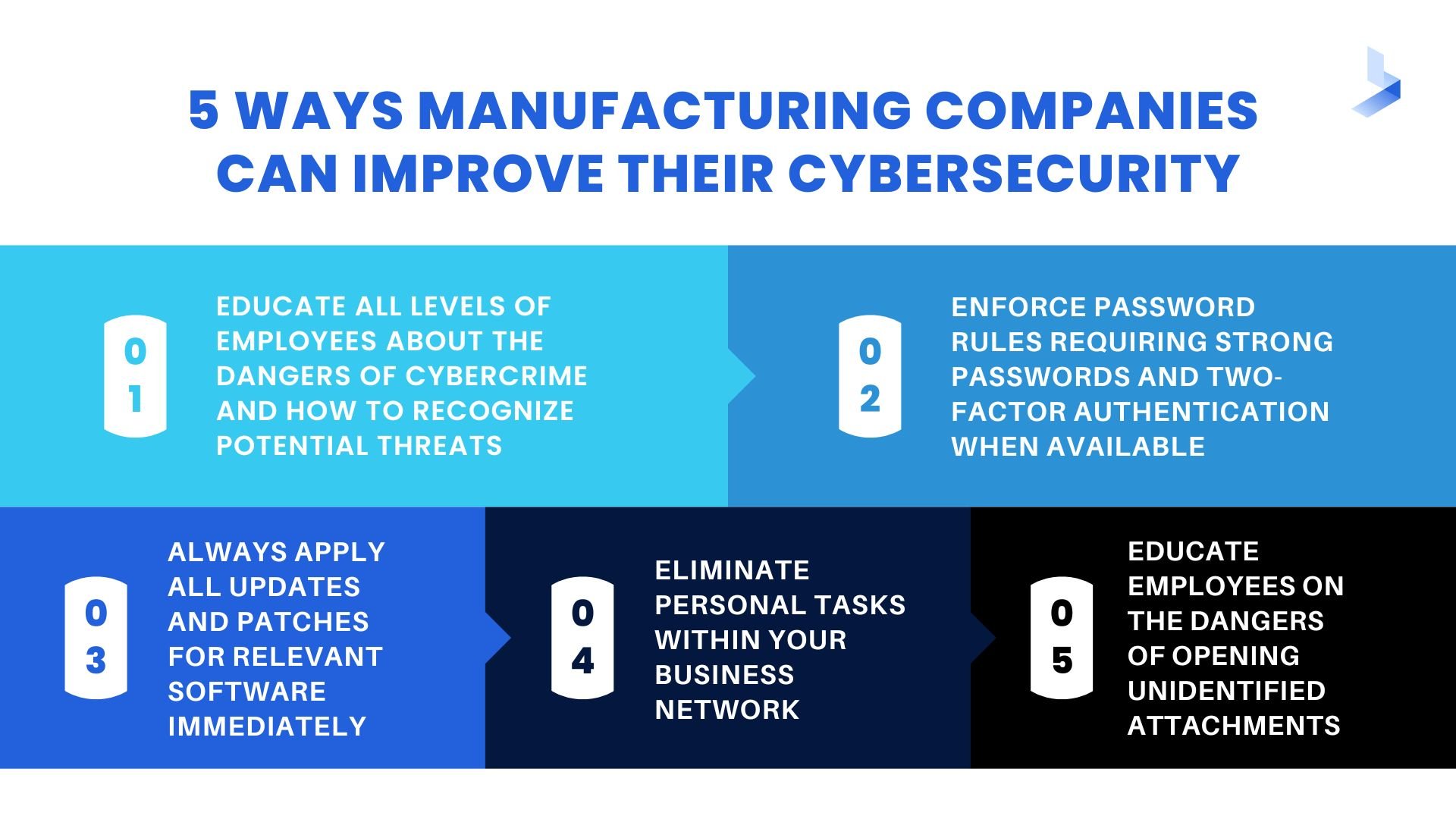
- Enforce password rules requiring strong passwords and two-factor authentication when available
- Always apply all updates and patches for relevant software immediately
- Eliminate personal tasks within your business network
- Educate employees on the dangers of opening attachments from an unidentified source
Utilizing a Complete Cybersecurity Solution for Protection Against all Types of Cyber Attacks
For most manufacturing companies, an in-house cybersecurity team isn't something that can fit within the budget. However, cybersecurity isn't a part-time job. Manufacturing companies with long supply chains and vulnerabilities due to fragmented systems need a comprehensive solution that provides complete visibility into the network, threat detection, and remediation plans for the inevitable moments when threats are identified within your network. A large portion of companies that aren't prepared for cyberattacks cite lack of funds as the biggest reason. Yet, manufacturing companies can't afford to skimp on cybersecurity.
For many small to medium businesses, hiring a third-party cybersecurity company is often a solution that provides the same type of protection as an in-house team. Advanced and automated solutions for threat detection and remediation provide visibility into your company's network to provide alerts to threats before they cause damage. Cybersecurity solutions from BitLyft combine security information event management (SIEM), automated responses to incidents, alerts, and threats (SOAR), and central threat intelligence that provides crowdsourced immunization for attacks that haven't reached your company. Third-party cybersecurity companies can help manufacturing companies perform a gap assessment, take steps to achieve necessary compliance, and avoid potential attacks.

Every manufacturing company needs a complete cybersecurity solution to remain protected from growing threats. Manufacturing companies have a variety of vulnerabilities exclusive to the industry. As threats grow, and companies address cybersecurity regulations enforced by NIST and outlined by recently introduced legislation, companies who fail to address cybersecurity will fall behind. Perhaps, even worse, these unprepared organizations will become an easy target for threat actors to exploit. To learn more about cybersecurity solutions and compliance regulations for manufacturing solutions, get in touch with the cybersecurity experts at BitLyft.



